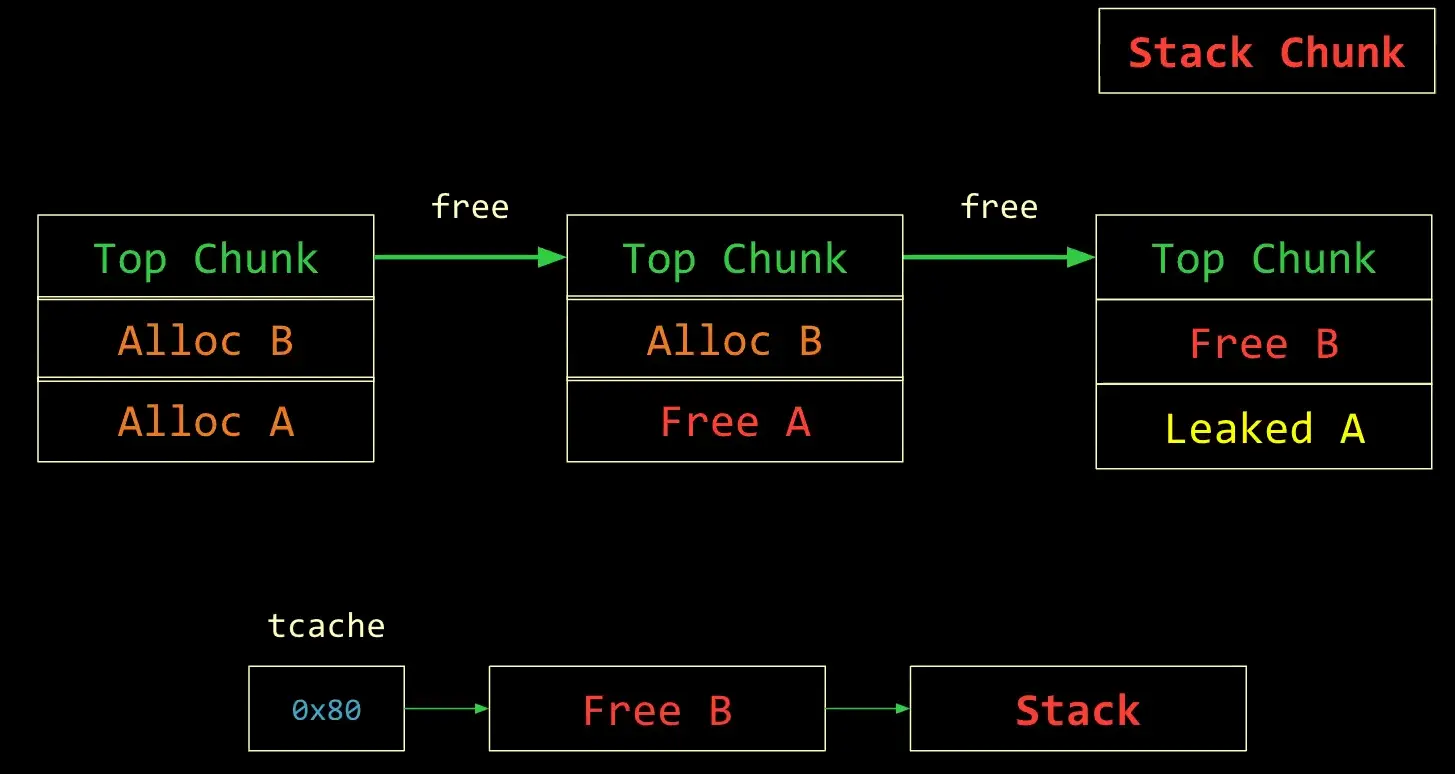
A heap attack that uses UAF to overwrite metadata of a Tcache Bin to point to a stack address that we can retrieve from a subsequent malloc
Example
- Malloc two times to get Heap Chunk

- Free these two chunks to get them into the Tcache Bin free list
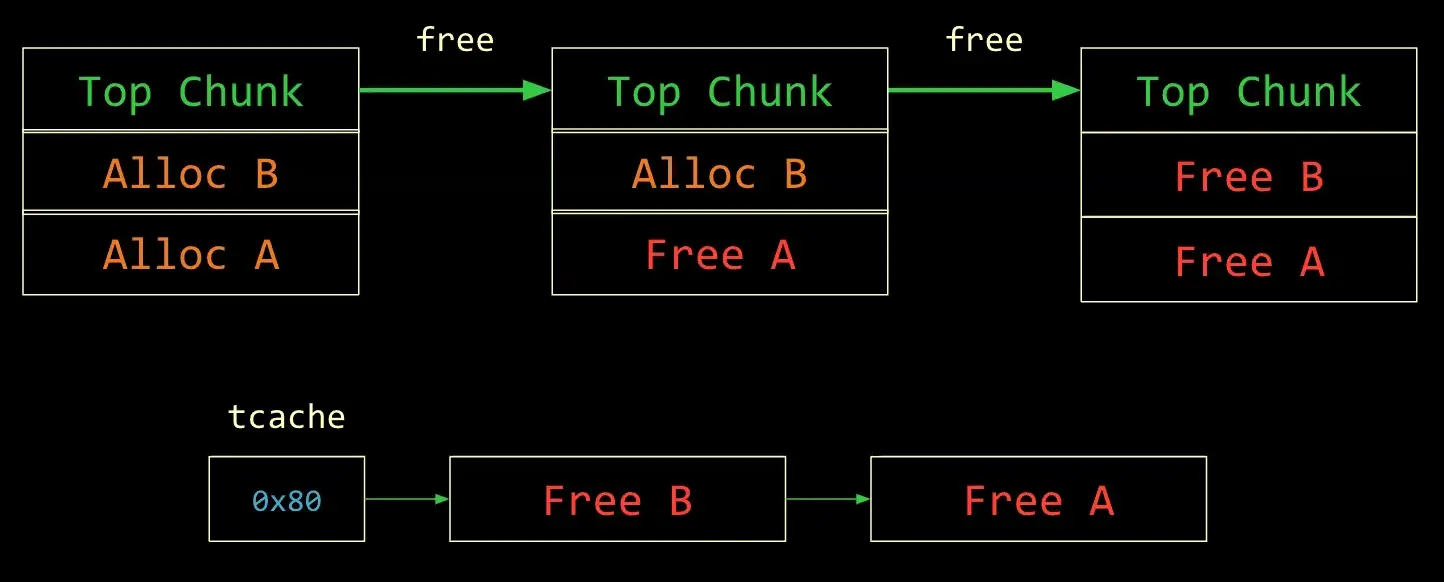
- Use UAF to corrupt B’s metadata

- Allocate a chunk, and get B, allocate another chunks and you get the stack’s address