Soln
We will use a Hex Editor
Note that there are a few comments. Lets highlight them
 Reading the file directly:
Reading the file directly:
%PDF-2.0
%SNDHNRO0ܧÄý]
£RE~^
% Hey there! Welcome to this source...
% Tested under the following browsers:
% Chrome, Safari, PDFjs (Firefox)
1 0 obj <<
% N0t_a_flag_but_just_a_line_comment
/Pages 2 0 R/Type/Catalog/Extensions <</ADBE <</BaseVersion/1.7/ExtensionLevel 8>>>>>>endobj
% 2 0 obj
% <<>>
% endobj
3 0 obj
<<
/Contents 4 0 R
/Parent 2 0 R
/Resources 6 0 R
/Type /Page
/MediaBox [0 0 612 130]
>>
endobj
2 0 obj
<<
/Count 1
/Kids [
3 0 R
]
/Type /Pages
>>
endobj
% 2 0 obj
% <<>>
% endobj
4 0 obj
<</Length 320/Filter /FlateDecode>>stream
±x¸l
ÝÄXY%�üکƯÜú¨?
Æ=þèÜÓm¹Á§µ
F³*ÌT/èlW8Úô¥¤/fÈAöâ´¡¡Î¯µð
þÍШ¤z
3ÿ
3zÌuØ~³öµæj5|.EÃ
ämõDÃWñ½Æ*g
μÒí×ì½tT#Â_äµ
'¢ßäó(Ò`íÂÝǧXõê ÖEéÈn#'x,ºÊd¨)1ÇÛÞ[
»G{౶{ióxP§m¢ßè
²âN Á5Rm Þ7>6*
´*}Oö
ufh¥á{µ\)R1 ûͪs�¡×]§U¸½=àsXÊøoʯSl�ÃÀúíD_X6^ÓíÐèé
endstream
6 0 obj
<<
/Font <<
/ <<
/BaseFont /Arial
/Subtype /Type1
/Type /Font
>>
>>
>>
endobj
7 0 obj
<</Filter /Standard/V 5/R 6/Length 256/P -1/EncryptMetadata true/CF <</StdCF <</AuthEvent /DocOpen/CFM /AESV3/Length 32>>>>/StrF /StdCF/StmF /StdCF/U (ümþßôµèäÂHÒ¼ø¶kë¼ÚÍ
cBT6fÒŤÃTYMñj12Jw)/O (v/Î^
3wéWXÆðÛ3ÆÜ0¤~A[ÜwvutmLl9W`Aiò
X«)/UE (Ò3gûe} ûJÄVwb¶ûÐr³WHa}?ë)/OE (Ý\\zRõC8éí¹Ëú¨gEòðmÂRÌÊõ)/Perms (G²KDǽµùHe´â)>>
trailer <<
/Root 2 0 R
/#52#6F#6F#74 1
% /Size 15
0
R
/Encrypt 7 0 R
>>We can ignore all the comments.
There are two objects of interest:
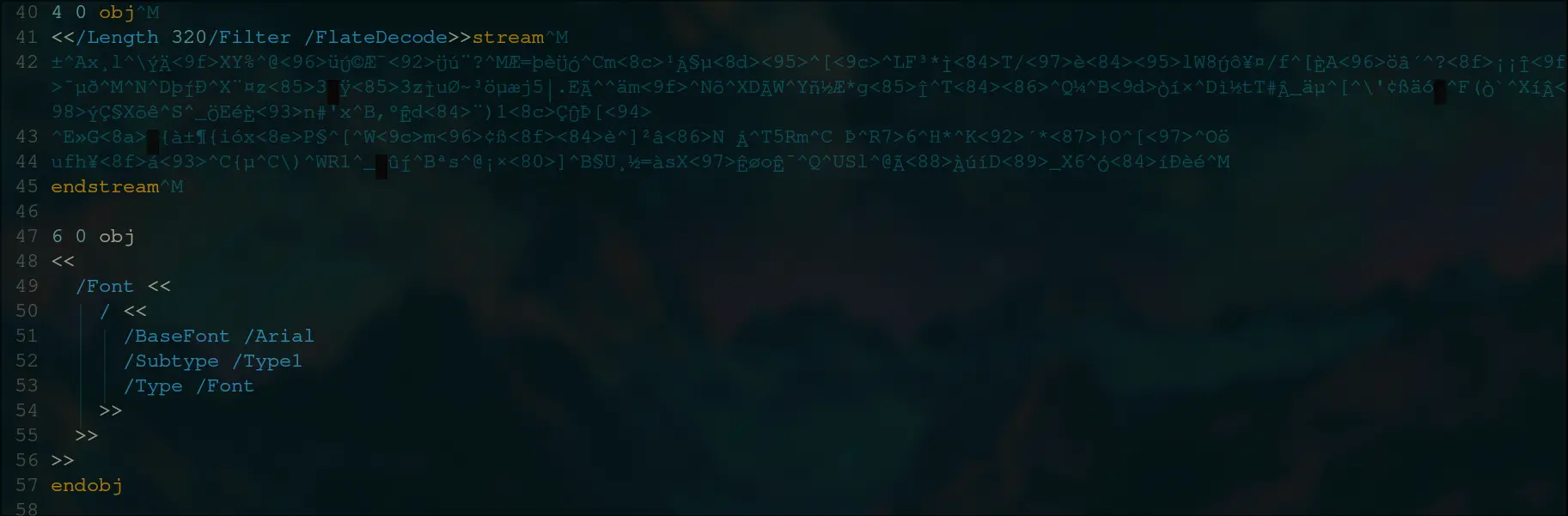
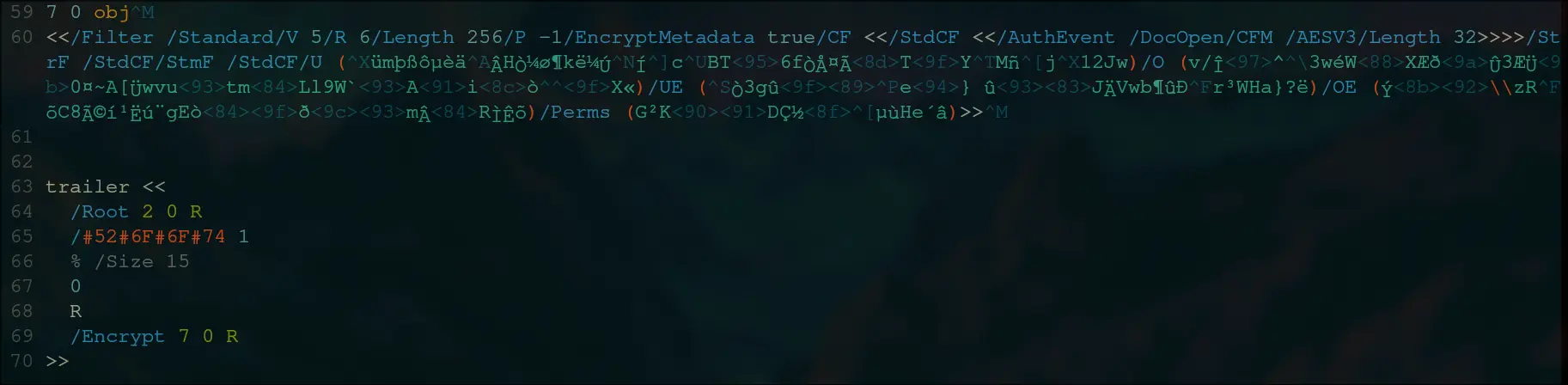 Lets try and decode the first stream and see what we get.
Lets try and decode the first stream and see what we get.
import re
import zlib
pdf = open("pretty_devilish_file.pdf", "rb").read()
stream = re.compile(rb'.*?FlateDecode.*?stream(.*?)endstream', re.S)
for s in stream.findall(pdf):
s = s.strip(b'\r\n')
print(zlib.decompress(s))
print("")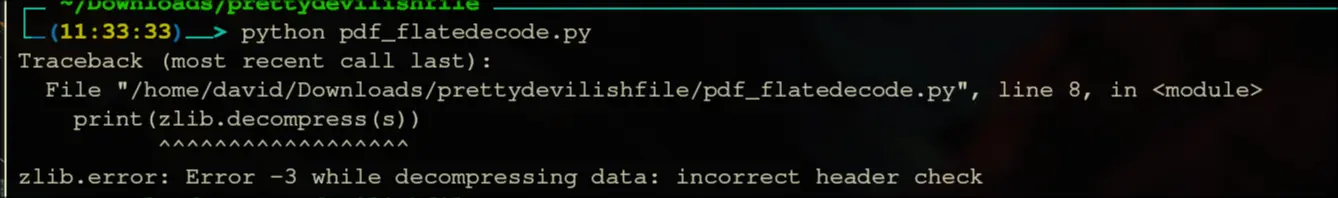 Well, it seems like that failed. I read this stack overflow article:
https://stackoverflow.com/questions/57260140/pdf-object-stream-with-flatedecode
Indeed, the PDF is encrypted, if we check at the end.
Well, it seems like that failed. I read this stack overflow article:
https://stackoverflow.com/questions/57260140/pdf-object-stream-with-flatedecode
Indeed, the PDF is encrypted, if we check at the end.
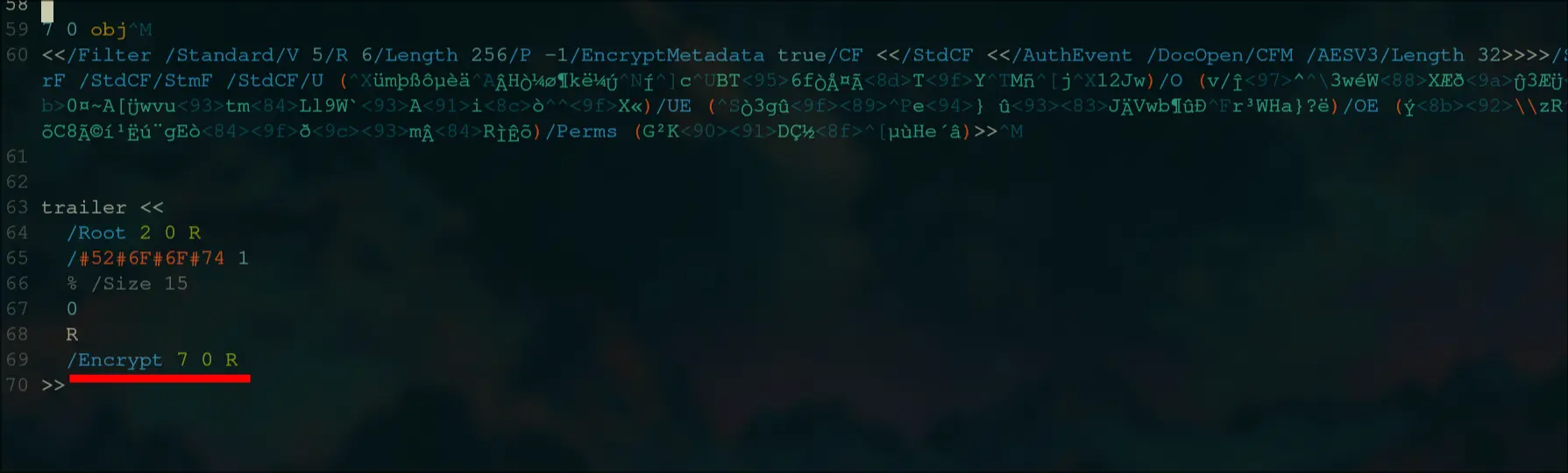 Now, there is something to note in the trailer.
/Root
and /#52#6F#6F#74 also represents root
The first root is pointing to the object reference 2 0 R, which is both commented and not commented, and is a tree object.
Now, there is something to note in the trailer.
/Root
and /#52#6F#6F#74 also represents root
The first root is pointing to the object reference 2 0 R, which is both commented and not commented, and is a tree object.
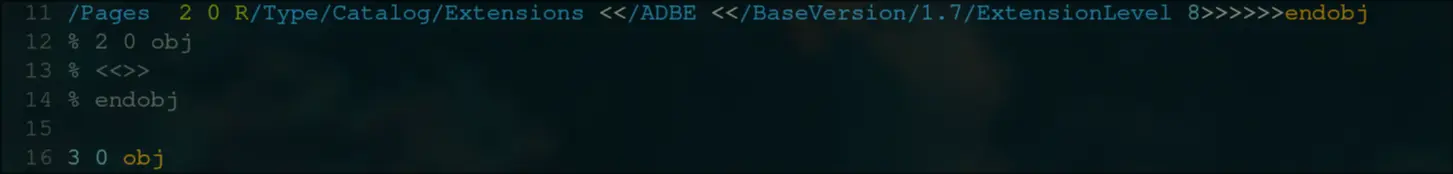 Lets try and change this root to 1 0 R instead.
No, no difference.
Object 7 is simple a dictionary with the current mappings:
Lets try and change this root to 1 0 R instead.
No, no difference.
Object 7 is simple a dictionary with the current mappings:
7 0 obj
/Filter /Standard
/V 5
/R 6
/Length 256
/P -1
/EncryptMetadata true
/CF <</StdCF <</AuthEvent /DocOpen/CFM /AESV3/Length 32>>>>
/StrF /StdCF
/StmF /StdCF
/U (encrypted_hash_data)
/O (encrypted_hash_data)
/UE (encrypted_hash_data)
/OE (encrypted_hash_data)
/Perms (encrypted_hash_data)
>>
endobj
PDF Restructuing
We can use qpdf to restructure the PDF:
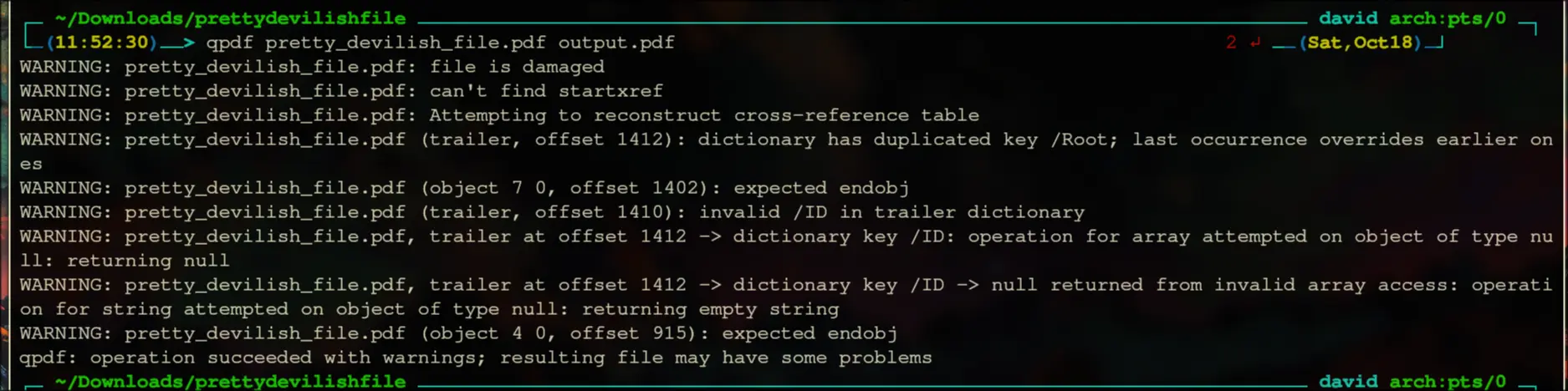 The new pdf is:
The new pdf is:
%PDF-2.0
%¿÷¢þ
1 0 obj
<< /Extensions << /ADBE << /BaseVersion /2.0 /ExtensionLevel 8 >> >> /Pages 2 0 R /Type /Catalog >>
endobj
2 0 obj
<< /Count 1 /Kids [ 3 0 R ] /Type /Pages >>
endobj
3 0 obj
<< /Contents 4 0 R /MediaBox [ 0 0 612 130 ] /Parent 2 0 R /Resources 5 0 R /Type /Page >>
endobj
4 0 obj
<< /Filter /FlateDecode /Length 320 >>
stream
tNr/
l´Ö8¥r¬³ ÎüÍrë'¾)Z`¤?_zÂ×
¶{WQÿûr`k
Î*Caîp fªfá
ó¾ü®nä
èÌÎj§;.÷ ³h`�ºÙÖ²*15ÓÊÞs¯¨5dÇ N½Ý')aÒÞ(ü@·Am
êø8v5ÍW=ñì¨Ú1µsQTrr5í0·Ç}×o
Sª¡5ã^,Ö5"(]³¯".@Æ,Sä"$¿»ý ®ý}Yûf±üÇÑÜ9Ä Wad»"?´WF¿IÆ
*Fg
¢¼§gȪK.r¬æWSR«ÀÔNðà>©k)ùÄ#
©$°ýPôýgÊfxk¤*°ý�BfH59/Uh;endstream
endobj
5 0 obj
<< /Font << / << /BaseFont /Arial /Subtype /Type1 /Type /Font >> >> >>
endobj
6 0 obj
<< /CF << /StdCF << /AuthEvent /DocOpen /CFM /AESV3 /Length 32 >> >> /Filter /Standard /Length 256 /O <762fce975e1c3377e9578858c6f09adb33c6dc9b30a47e415bdc77767593746d844c6c395760934191698cf21e9f58ab> /OE <dd8b925c7a5206f54338c3a9edb9cbfaa86745f2849ff09c936dc28452cccaf5> /P -1 /Perms <47b24b909144c7bd8f1bb5f94865b4e2> /R 6 /StmF /StdCF /StrF /StdCF /U <18fc6dfedff4b5e8e401c248d2bcf8b66bebbcda0ecd1d63154254953666d2c5a4c38d549f59144df11b6a1831324a77> /UE <13d23367fb9f891065947d20fb93834ac4567762b6fbd00672b35748617d3feb> /V 5 >>
endobj
xref
0 7
0000000000 65535 f
0000000015 00000 n
0000000130 00000 n
0000000189 00000 n
0000000295 00000 n
0000000686 00000 n
0000000772 00000 n
trailer << /Root 1 0 R /ID [<><524fc2d386a8e0a36a62eb8904aac89a>] /Encrypt 6 0 R >>
startxref
1319
EOF
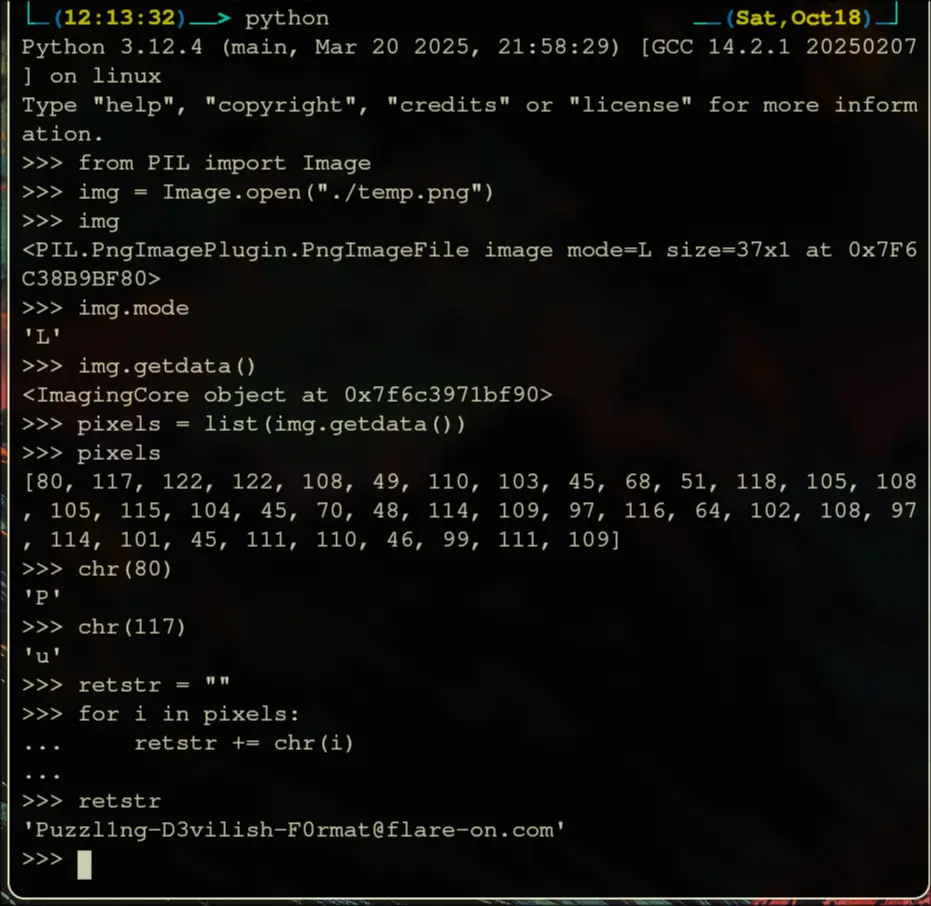
There is an image file in here. We can take the hex code and convert it into an image:
 Open into gimp:
Open into gimp:
 Its a grayscale image.
Lets view the bytes:
Its a grayscale image.
Lets view the bytes: